- Lancez Google Earth.
- Dans la barre d'outils, cliquez sur l'icône en forme de planète.

- Dans la liste qui s'affiche, sélectionnez l'option Mars.

- Vous pouvez alors vous balader sur la planète, comme sur la Terre, zoomer en avant, etc.

- Notez
que les infos pratiques à gauche se sont adaptées à la planète. Vous
pouvez ainsi afficher par exemple les emplacements des différentes
sondes, lancer une visite guidée, etc.

Pro Téch
dimanche 20 janvier 2013
Faire du tourisme sur Mars - Google Earth
Avec Google Earth, vous connaissiez certainement la fonction Sky pour
naviguer dans l'espace. Vous pouvez aussi visiter la planète Mars sous
toutes ses coutures, comme vous le faite avec la Terre.
lundi 14 janvier 2013
Faire des calculs sur les dates

Vous souhaitez savoir l'âge que vous avez en jours ? Combien de jour il reste avant Noël ? Avec l'outil Calcul de la date de la calculatrice Windows, c'est facile.
- Cliquez sur le bouton Démarrer, saisissez Calc et validez par Entrée.

- Cliquez sur le menu Affichage puis cliquez sur Calcul de la date.

- Sélectionnez l'option Calculer la différence entre deux dates.

- Spécifiez les dates de début et de fin.

- Cliquez enfin sur Calculer. La calculatrice vous indique alors la différence en jours entre les dates.

- La calculatrice vous permet également d'ajouter ou soustraire
des jours à une date spécifique pour voir le jour correspondant.
Sélectionnez pour cela l'option Ajouter ou soustraire des jours à une date spécifiée.

- Spécifiez la date de départ puis l'opération que vous souhaitez effectuer : Ajouter ou Soustraire. Indiquez ensuite le nombre d'années, de mois et de jours à ajouter.

- Cliquez enfin sur Calculer. Le jour correspondant est affiché.

dimanche 13 janvier 2013
Etre prévenu lorsque quelqu'un met votre nom sur une photo - Facebook

Si n'importe quel ami peut signaler que vous figurez sur une photo publiée sur Facebook, vous pouvez être alerté à chaque fois que cela se produit. Vous pourrez ensuite retirer votre tag sur les photos en question.
- Rendez-vous sur Facebook et identifiez-vous.

- Cliquez sur la flèche à côté d'Accueil et cliquez sur Paramètres du compte.

- Cliquez sur Notifications.

- Si cela n'est pas déjà fait, décochez la case M’envoyer les
mises à jour importantes et des récapitulatifs par courrier
électronique au lieu de messages électroniques individuels.

- Cliquez sur Photos.

- Cochez alors la case Indique que vous vous trouvez dans une photo.

- Cliquez ensuite sur Enregistrer les modifications. Vous recevrez alors un email à chaque fois que quelqu'un ajouter votre nom sur une photo.

Retrouver sa clé WiFi depuis une machine connectée - Windows 7

Votre ordinateur est connecté en WiFi à votre box ou votre routeur. Vous avez besoin de connaître la clé WiFi pour connecter un autre ordinateur sans fil mais impossible de vous en souvenir. Il est possible de la récupérer dans vos paramètres de connexion.
- Pressez simultanément sur les touches Windows et R.
- Dans la fenêtre Exécuter qui s'affiche, saisissez la commande ncpa.cpl et validez par Entrée.

- Cliquez avec le bouton droit de la souris sur l'icône de votre connexion wifi et cliquez sur Statut.

- Cliquez ensuite sur le bouton Propriétés sans fil.

- Ouvrez l'onglet Sécurité.

- Cochez alors la case Afficher les caractères.

- Votre mot de passe est affiché en clair dans le champ Clé de sécurité réseau. Validez enfin par OK.

dimanche 23 décembre 2012
Faute d'accord, Google et la presse ont un mois pour s'entendre

Le gouvernement a donné un mois supplémentaire aux éditeurs de presse français et au géant américain Google pour trouver un accord sur l'éventuel paiement de "droits voisins", a indiqué vendredi à l'AFP une source proche du dossier. Depuis début décembre, les représentants du moteur de recherche et ceux de l'association de la presse d'information politique et générale (IPG) se réunissent sous l'égide du médiateur nommé par le gouvernement, Marc Schwartz, du cabinet de conseil Mazars.
Les éditeurs de presse exigent que Google paie des "droits voisins" du droit d'auteur, au regard des importants bénéfices publicitaires qu'il réaliserait en référençant leurs titres. Le président de la République François Hollande, qui avait reçu à la fin octobre le patron de Google Eric Schmidt, avait annoncé qu'une loi pourrait "intervenir si nécessaire" pour faire payer une taxe à Google, dans l'hypothèse d'un échec des négociations avant fin décembre.Jeudi, une "réunion de la dernière chance" n'a pas débouché sur un accord, mais le gouvernement a décidé vendredi d'accorder un mois supplémentaire à la médiation, en donnant jusqu'à fin janvier aux deux parties pour s'entendre, selon la source proche du dossier. A la mi-octobre, Google menaçait de ne plus référencer les médias français s'il devait se voir imposer une taxe assimilée à des droits d'auteur. Selon la Correspondance de la presse de jeudi 20 décembre, le gouvernement a déjà prévu, dans son programme législatif pour le premier semestre, un projet de loi instaurant un droit voisin du droit d'auteur au cas où cette médiation entre Google et les éditeurs échouerait.
Google vend une division de Motorola

La réorganisation du pionnier de la téléphonie mobile Motorola se poursuit. Sa maison-mère, Google, a vendu, jeudi 20 décembre, la division Motorola Home à l'équipementier en télécommunications Arris pour la somme de 2,3 milliards de dollars (1,7 milliard d'euros). La vente de cette division, à l'origine des décodeurs TV de Motorola, confère à Google une part de 15,7 % dans Arris.
Google, qui a bouclé le rachat de Motorola Mobility en mai pour 12,5 milliards de dollars (9,5 milliards d'euros), a entrepris de recentrer l'entreprise en difficulté. La firme de Mountain View a ainsi annoncé le licenciement de 4 000 employés en mai, ainsi que la fermeture de la branche israëlienne de Motorola en août. Ces mesures s'accompagnent d'un recentrage de l'activité du constructeur de téléphones sur le haut de gamme, notamment les smartphones RAZR, utilisant le système Android de Google.
Google a avant tout acquis Motorola pour son large portefeuille de plus de 17 000 brevets. La filiale est devenue le bras armé du groupe dans la guerre des brevets, notamment contre Apple et Microsoft. Les entreprises se sont d'ailleurs affrontées récemment devant des tribunaux européens. Les brevets de Motorola sont également censés servir à d'autres constructeurs de terminaux Android confrontés à Apple ou Microsoft, alors que Google compte devenir plus agressif dans ses dépôts de brevets.
dimanche 16 décembre 2012
Google Adsense Terms Privacy Policy Generator for Publishers
As an adsense publisher I didn't noticed about the TOS (Term of Service) carefully that tells by Google I should put "Privacy Policy" on my Blog, until I found this link. But Thanks's God finally I put and protect my Google Adsense from any "Double Click" that causes from Browser cookies or web beacons. If you're don't undertsand what I'm talking about go had to read this article until you finish it.
As Google have changed the Terms and Conditions of their Adsense program (Update: 23 March 2009), one of the requirements now is that all Adsense publishers should have a "Privacy Policy" on their websites. Below is the exact wording that has been added to the Terms and Conditions for Adsense publishers. it's been says: If you don't agree with the new term conditions , you'll be banned of the Google Adsense program.
Check out what Google says about the term of condition:
So, If you're new to hear this like me, and you want to avoid kicked by Google adsense you should include this "Privacy Policy" that puts on your Blog/website. to do that you can visit http://www.google.com/privacy/ads/ or if you don't understand how to do that, you can use Google Adsense Generators provided by serprank.com
As Google have changed the Terms and Conditions of their Adsense program (Update: 23 March 2009), one of the requirements now is that all Adsense publishers should have a "Privacy Policy" on their websites. Below is the exact wording that has been added to the Terms and Conditions for Adsense publishers. it's been says: If you don't agree with the new term conditions , you'll be banned of the Google Adsense program.
Check out what Google says about the term of condition:
"You must have and abide by an appropriate privacy policy that clearly discloses that third parties may be placing and reading cookies on your user’s browser, or using web beacons to collect information, in the course of ads being served on your website. Your privacy policy should also include information about user options for cookie management."
So, If you're new to hear this like me, and you want to avoid kicked by Google adsense you should include this "Privacy Policy" that puts on your Blog/website. to do that you can visit http://www.google.com/privacy/ads/ or if you don't understand how to do that, you can use Google Adsense Generators provided by serprank.com
Why to Purchase a Desktop PC Instead of Laptop? Desktop PC's VS. Laptops
How to Know If You Need a Desktop Computer?
Computers come in all different sizes — from desktops to laptops and tablets to smartphones. So, you can pretty much choose any size you want. There are times, however, when only a desktop computer will suffice, like when you need a stable computer with access to a printer, router, and other equipment that can’t be moved very easily. Don’t fret though; there are several advantages to owning a desktop computer. Take a look at some reasons why you might need a desktop computer instead of a laptop.
Computers come in all different sizes — from desktops to laptops and tablets to smartphones. So, you can pretty much choose any size you want. There are times, however, when only a desktop computer will suffice, like when you need a stable computer with access to a printer, router, and other equipment that can’t be moved very easily. Don’t fret though; there are several advantages to owning a desktop computer. Take a look at some reasons why you might need a desktop computer instead of a laptop.
You Want the Best Features and Components
Because desktops don’t have a limited amount of space, they can give you
more features than smaller computers. Yes, the portability of tablets
is definitely appealing, but desktops have plenty of unique features
that are appealing, too, like the following:
- Large Screen Size: Laptops are limited to a 17-inch, max screen size. With a desktop computer, though, you can buy a monitor that takes up the entire desk. Or, have two monitors, if that’s what you prefer.
- More Storage Space: Since desktop computers don’t have to fit in compact dimensions, they have more space available for hard drives and other components. This means you can have a terabyte or more of storage space without much effort.
- Faster Speeds: Faster processors tend to be larger, so they are more commonly found in desktop computers than laptops or other portable computers. So overall, your desktop computer should run faster than a laptop.
You Don’t Want to Spend an Arm and a Leg
Another reason to purchase a desktop computer is that they tend to cost less than laptops with the same features. So, you can buy a better computer for the same amount of money as a laptop. Laptops tend to cost more because they are newer technology that is more in demand. If you need a desktop computer, you might as well take advantage of the cheap prices. You can find many great deals on affordable ultrabooks and laptops just in time for the holidays!
You Want Your Computer to Be Secure
You’re more likely to have your laptop stolen than your desktop PC
simply because of size. Just think about it — desktop computers weigh at
least three times as much as laptops. Plus, you can secure your desktop computer to your desk with a cable for extra protection, whereas this really isn’t practical with a laptop.
Other Reasons You Might Need a Desktop Computer
The speed, cost, and security aren’t the only things you might be looking for in a computer. If you plan on doing any gaming, you’ll want to upgrade the graphics card
and buy better quality speakers. Additionally, you might need to make
sure your desktop has wireless and Bluetooth capabilities, or even a
built-in TV tuner.
So, once you’ve decided that you need to buy a desktop computer instead
of a laptop, make sure you choose one that will work best for you. Be
sure to get one with the best processor available and as much ram and
hard drive space as you can afford. You’ll also want to do a lot of
research to determine the most important features you need.
Things to Consider When Rooting an Android Phone & Tablet Devices
When mobile device manufacturers adopt an operating system, the full potential of the device in not used and they set limitations over the functionality, for reasons like security and business interests. Similarly, phones that run Android
have limitations too. To overcome this limitation and gain access to
system level operations, you need certain privileges. Since Android is a Linux based operating system, you need root password to gain control and the process
of attaining these privileges is known as rooting. The legality of
rooting has been a subject of debate and the American law clearly states
that rooting is not illegal and neither is the unlocking of mobile phones to work with other operators.
The process of rooting an Android device is fairly easy and once it is
done you can install third party firmware and tweak pretty much
everything there is to tweak. Initially when Android phones hit the market, rooting was only for the crazy brave and phony tough, but now, there are tool kits
with graphical user interface that can root every single Android device
out there. We are not going to discuss about the steps involved in
rooting here and rather, we will look into the things that you need to
consider before rooting your Android device.
Manufacturer warranty:
Although it is legal to root an Android phone or device, manufacturers
do not appreciate it when you do it. If you go through the End User
License Agreement, you will know if the manufacturer voids the warranty
if you root it. You will have to realize that rooting is not a
reversible process where you can restore the device. Once you root the Android device, the super user permissions are permanently saved.
Know your device:
Before you download a rooting tool kit and start the process,
take some time to know about the version of Android that your device
runs. Each version of the mobile operating system has a different
exploit method and you might run into the risk of bricking (rendering
your phone or Android device unusable) and it is very hard or sometimes
impossible to bring it back to life. Also, read the release statement
that comes along with the rooting tool kit to make sure that your device is supported.
Security:
Rooted Android devices in the past have been very unstable and crashed
often. Moreover, since the root password is open, the chance of a security breach is possible and this brings financial applications and secure transactions to be generally avoided.
Backing up:
This is possibly the most important aspect that you need to consider
before rooting the Android device and it is the data that you have
stored on the flash memory. Although there is a separate partition for
the operating system, there are chances that the data on your phone will
be wiped out. So back up all your contacts, calendars, appointments,
reminders and pictures before you begin rooting the device.
Before you begin rooting the Android device, these are the most important things that you need to consider.
Top Predicted Information Technology Trends of 2013
Taking a cue from Red Queen’s advice to Alice, technology and the people
powering technology seem to be running twice as fast as they can with
an intention of getting to someplace new. With 2012 coming to a close,
everyone is busy making their predictions and giving the quintessential
finishing touches to their 2013 wish-list and why not? 2012 managed to
give us a taste of what to expect from 2013. The year 2012, with much
groundbreaking advancement in technology changed the way we interacted
with each other. It brought mobile technology within the reach of the masses. We saw great innovative products, bitter one-upmanship wars, clever marketing
strategies and unfathomably new technologies. While some companies had
roaring success with their products, the others received an icy-cold
response from the consumers. Nevertheless, with what we have seen in
2012, we can only assume that the next year will be equally great, if
not better.
A new nomenclature in town- the Phablet! (No.1 Tech Prediction of 2013)
Here is a list of our Top Six Predictions for Information Technology Trends in 2013.
A new nomenclature in town- the Phablet! (No.1 Tech Prediction of 2013)
With the advent of smartphones
and the concept of multi-touch, the world of mobile communications
changed forever. Communications and computing underwent a drastic change
with the launch of the iPhone and the iPad. Developers around the world
were seen jostling against each other to develop the perfect mobile
device that can bring the best of smartphones and tablets in to one
great product.
Thus, the idea of creating a product that will act as a bridge between
smartphones and tablets came about - the Phablet. The Phablet acts both
as a tablet and as a smartphone but with a larger screen and lesser
price. Phablet’s growing popularity shows that the future for it is
certainly good. With Apple and Google showing keen interest in
developing phablets, 2013 may see them taking over consumer markets.
More Voice Assistants - Siri and her family: (No.2 Tech Prediction of 2013)
There are times when you have been typing the whole day and come to a
point where you can’t type any more. A voice assistant who can type what
you say would be a welcome idea if it can save you from spending
innumerable hours typing. Yes, this was the idea behind Siri. But, Siri
has a long way to go. And in 2013, we may see a lot more of a refined
Siri and Siri-like voice assistants.
Apple is making Siri more equipped to handle voice commands, interpret
human speech nuances and recall previous commands and results. Siri has
been a great start but 2013 may bring in many more Siri’s for everyone.
NFC for everyone: (No.3 Tech Prediction of 2013)
NFC technology, predicted by experts as the future of smartphones never
seemed to catch fire. But with Apple’s iPhone 5 bringing NFC tech to
consumers, analysts predict NFC to be the future of data transfer. NFC
has been implemented in most Android smartphones too.
NFC technology enables wireless transactions between mobile devices. The
need for data cards is completely negated when NFC is used for data
transfers and commercial transactions. By pairing devices close to each
other and tapping on products, files or data will get transferred from
one phone to the other.
Technology gets a gut-feeling- the Sixth Sense Technology: (No.4 Tech Prediction of 2013)
The Sixth Sense Technology has been around for quite some time now but
it really hasn’t been exploited much. That may well change in 2013. The
ability to read information from the Internet and project it on to a
wall and using gestures for manipulating daily activities
can be fantastic. To better understand the concept of Sixth Sense
Technology, imagine taking pictures using simple hand gestures. We are
hoping that the year 2013 will see sixth sense technology materializing.
A virtual Keyboard: (No.5 Tech Prediction of 2013)
We have seen chiclet keyboards, the TypeCover and the TouchCovers and
thought that keyboards can’t get any savvier. But, with infrared
keyboards and holographic keyboards on the offing, we may be compelled
to change our views. They certainly look unrealistic and unlikely but
hasn’t every new technology started on the same road? With Apple filing a patent on the design for projectors similar to Pico, the idea behind virtual keyboards will have a shot at reality.
Cloud Computing on cloud number nine: (No.6 Tech Prediction of 2013)
Everyone these days, seem to be on cloud nine. The future of mobile technology will rely on cloud computing. Hybrid clouds and personal clouds will become common terms in the field of computing. Cloud Computing will harmonize and increase the use of all mobile devices from smartphones to tablets.
While the last few years have paved the way for today’s mobile
technology, the smartphones and tablets of today will certainly shape
the future. With everyone turning into modern-age Nostradamus
predicting the direction in which information technology is going to
go, the future of mobile technology is anything but mundane. We have
listed a few predictions and trends for 2013, but the best thing about
future, as they say, is that it has begun already. The future is here.
Are we ready to greet it?
How to Scan Websites & Blogs for Malicious Code to Avoid Hacking?
If you will look around and research on the internet, you will find so many websites and Blogs that are infected by some malicious code or have been hacked. In most of the cases, hackers place such codes in your website that can help them get into the settings of your website and hack it whenever they want. Those hackers are very clever to use such attributes in codes due to which a website owner will never get to know about any trespassing.
If you are not sure what is embedded in your website in the form of code then Google will definitely get to know about it. However, once you figure out that there is something fishy going on with the internal health of your website, you need to get it scanned and rule out of any chances of having some malicious code in it.
If you are not sure what is embedded in your website in the form of code then Google will definitely get to know about it. However, once you figure out that there is something fishy going on with the internal health of your website, you need to get it scanned and rule out of any chances of having some malicious code in it.
How to check if you have malicious content on your website and blogs?
A friend of mine got hacked recently not one time but two times in a
row. For the first time when he got over that issue, he was happy that
the problem is over but after a few hours, his website was hacked again.
That is when he realized that the hacker had left some malicious code on his website and that was giving that hacker a backdoor to enter into this site and hack it over and over again. In order to find a malicious code
on your website, you need to take a look at the source code. If you are
not a developer, ask your web developer to take a look at the code and
find out anything that is not supposed to be there.
How to Remove Malicious Links from Websites and Blogs?
After figuring out the problem or code that is causing your website to
get hacked, change the entire source code of your website. The simplest
thing that you can do is to rewrite the parts in which hackers had embedded their code. Now upload the new source code to your server so your website can become free from any malicious codes.
After doing all these things, you need to take preventive measures in order to keep your website safe from hackers in future. Keep in mind that if you will not set up high security on your site, any hacker will be able to find a backdoor in order to enter your site and change things the way he wants.
If you are running your website on WordPress then you can use different plugins to check your website for any malicious code. Some of the best plugins are described below.
TAC – This plugin can check the authenticity of your theme. Install this plugin to scan all the themes that are present in your database to rule out any malicious code that may be present in those themes.
Antivirus – This is very easy to use WordPress security plugin that can easily scan your themes and other files for malicious codes and remove them.
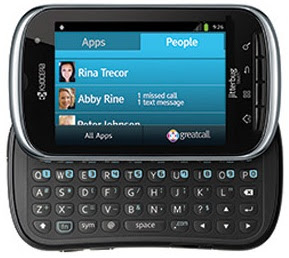
GreatCall's Jitterbug Touch Smartphone Review
The design of the GreatCall's Jitterbug Touch is identical to that of the Kyocera Milano.
It’s round and a little bulky, with the back panel a dull gray
soft-touch plastic. The display is a 3-inch, 320-by-240-pixel touch
screen which makes it one of the lowest res displays for a Smartphone.
The small screen coupled with the poor resolution makes for blurry images. It’s a little better at max brightness. When you slide it open you get a QWERTY keyboard
set in 4 rows. The keys are decently sized, elevated and backlit.
Typing is easy enough, but given the size of the phone, it’s no typing
paradise. There are four physical keys beneath the display; you also
have a power button and a headphone jack on the top, volume control and
power port to the left, and a camera shutter button on the right side. This is supposedly a 3G Smartphone,
but in reality, does not hit the requisite speeds. The plus side is
that since GreatCall’s data plans are diminutive, you can be sure you
won’t exceed your limit!
GreatCall’s Jitterbug Touch Voice quality is nothing to rave about, with
scratchy sounds in the earpiece, though not unintelligible. Noise
cancellation left a lot to be desired and the caller’s voice went across
a little muted. The phone can be used by people wearing hearing aids, and it also has a good speakerphone. Battery life is close to ten hours. The Jitterbug Touch runs on Android 2.3.4 (Gingerbread).
That’s a bit of a downer, but it has been tweaked a little, so it’s
decent. On switching the phone on, you see 2 tabs on the top of the
screen: Apps and People which along with menus are arranged in large
font scroll down lists; you can see easily what your phone is capable
of. ‘Apps’ has a list of your most used applications like Phone,
Messaging, Camera, and Gallery. You can of course, modify the list
according to your wish. The People tab is for storing your favorite
contacts. You also have touch buttons at the bottom to access All Apps
and GreatCall services. GreatCall lets you access features like Featured
Apps, Usage, Contact and Help. If you select Contact, you can talk to a
customer care representative to help with any issues you have. Pressing
Help gives you a descriptive list of instructions on how to utilize
your phone, and Featured Apps displays MedCoach Android apps and GreatCall's 5Star, with a few others. The UI has got a few bugs like displaying the wrong name, and the old Android lock screen on boot up. Bluetooth pairing is also a bit difficult.
GreatCall’s Jitterbug Touch is powered by an 800MHz Qualcomm chip, and compared to other Android phones,
is a little slow, especially navigation and opening apps. Built-in
storage is 90 MB along with a 2 GB micro SD card. All music file formats are not supported, though sound quality is pretty decent. There’s a 3.2 MP auto focus camera minus LED flash, and the picture
quality is lackluster. While the phone itself is nothing to whoop and
holler about, GreatCall’s plans and assistance services make this a
great option for seniors and those in poor health and living alone. The
Jitterbug Touch costs $169 and is available directly from GreatCall's website.
Les technologies Web et les tendances à surveiller en 2012
L’année dernière le même article
était classé à la deuxième position du top 5 des plus visités sur le
blog ! C’est donc un sujet qui vous plait… C’est pourquoi, en ce début
d’année, je vais de nouveau parler des technologies Web et les tendances à surveiller pour 2012.
2012 s’annonce être une année intéressante ! Le contexte économique
actuel oblige les entreprises du monde entier à fermer, et apparemment
ce n’est pas prêt de changer… De plus, de nombreux gouvernements font de
leur mieux pour censurer l’Internet, bafouant les droits fondamentaux
des citoyens.Pour la conception et le développement Web, 2012 pourrait être toute aussi mouvementée. Nous sommes au milieu de différentes escarmouches : le mobile continu d’engloutir goulûment les parts de marché sur les ordinateurs de bureau, les applications natives menacent les aspects du « Web ouvert », de nombreuses informations sont désormais disponibles aux yeux de tous, il y a une consolidation de la fragmentation, et enfin, on trouve au sein des interfaces l’adoption de nouvelles méthodes innovantes de conception et de présentation de l’information et du contenu.
À moins de posséder une boule de cristal et savoir s’en servir, il est difficile de prédire exactement ce que nous réserve le futur, mais un certain nombre de designers, développeurs et les chiffres de l’industrie nous donnent des indices. Voici mes prédictions sur les années à venir, et les tendances que vous devez être conscient de savoir pour réussir vos futurs développements.
Amélioration progressive
Aujourd’hui, la montée en puissance de la téléphonie mobile et la dominance de Webkit au sein des smartphones, par rapport à la navigation Web traditionnelle sur les ordinateurs de bureaux, sont très convaincantes. Même les sceptiques purs et durs, commencent à soutenir l’amélioration progressive, c’est-à-dire prendre en en compte l’accessibilité, la sémantique et le référencement. HTML5, CSS3, et d’autres principes et aspects des normes y contribuent.De plus, IE, longtemps décrié, c’est tourné vers l’avenir en soutenant désormais pleinement les normes. C’est un signe fort sur cette ruée vers un nouveau « monde » du Web.
Une conception adaptée (Responsive design)
Nous sommes également confrontés à un gros problème de normes, mais dans l’espace matériel. En effet, il y a une pléthore d’appareils avec des capacités très différentes. Il n’a jamais été plus confus et difficile de créer des interfaces léchées qui fonctionnent sur tous les dispositifs. Ainsi, nous devrions voir la conception adaptée jouer un plus grand rôle en 2012, et ce afin de combler au maximum l’énorme écart entre les plates-formes.Si un site doit diminuer en taille, cela ne signifie pas que toute l’information sur une version de bureau soit aussi précieuse que celle d’une version mobile. Le type d’informations proposé aux utilisateurs pour lesquelles il peut interagir doit également être ajusté autant que la taille du site lui-même.
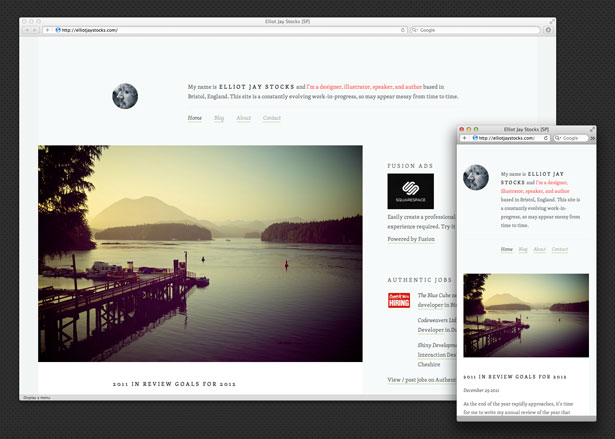
Ainsi, en 2012 nous devrions voir de nombreux projets dont le contenu se verrait adapter à la taille de l’écran. On aurait donc une stratégie appropriée dont le contenu affiché serait dicté par les différentes résolutions.
Flash va survivre…
Beaucoup disent que Flash en 2011 va disparaître… Pourtant, on pourrait voir du nouveau pour la technologie d’Adobe en 2012. Beaucoup de gens soutiennent l’idée de ne pas créer de sites Flash, favorisant les standards du web, et je suis moins enclin à l’utiliser de nos jours. Cependant, je crois néanmoins qu’il est là pour rester pendant un moment.D’ailleurs, durant l’année 2011, Flash a été impliqué dans trois grands projets, simplement parce qu’il demeure le meilleur outil pour la vidéo et les animations 3D interactifs en ligne.
Les concepteurs et les développeurs Web perdent parfois de vue ce qui fonctionne et est demandé par un large public, en raison de préférer ce qui est considéré « cool ». Certes nous devrions voir de plus en plus de développement en HTML5/CSS3, notamment pour des campagnes ciblées, mais pour les sites de divertissement, Flash est – et restera – l’outil prépondérant de choix et ce, afin d’avoir une bonne expérience utilisateur.
Alors certes les clients cherchent à orienter les choses vers l’HTML5, notamment grâce à un gros battage médiatique, mais je pense que Flash sera encore utile pour de nombreux projets.
Le support des fonctionnalités natives
Même si Flash prospère en 2012, la marche à suivre des navigateurs est de poursuivre le développement des fonctionnalités natives comme l’indique Bruce Lawson, évangéliste des standards ouverts du Web pour Opera :The new age of the internet
Silicon Roundabout in Old Street. The internet economy is worth more than 8% of UK GDP. Photograph: Oli Scarff/Getty Images
According to the Boston Consulting Group, by 2016, 3 billion people will be online and the internet economy will be worth $4.2tn among G20 countries – almost doubling in size since 2010. It's a revolution which is rewiring every part of business and society, from SMEs to multi-nationals, not-for-profits to governments – and Britain is leading the way. In 2010, the internet accounted for more than 8% of UK GDP (a figure I'll come back to), more than any other G20 nation, including the US (at 5.4%) and China (6.9%). We spend three times as much on e-commerce as any other country and double the amount on online advertising – so the impact on retail and media is more profound in the UK than anywhere else. Moreover, the online economy here is predicted to expand more quickly than in the world's two biggest economies.
Nowhere is that growth more clearly demonstrated than in Tech City, east London's technology quarter. Over the past two years, the number of internet-based companies located in the Old Street area, has quadrupled to more than 800. Not only is London firmly established as a social media hub – it is the only English-speaking city in the top 10 global cities for Facebook users and the No 1 world city for Twitter – but internet giants including Amazon, Facebook, Google, Skype, Twitter and Yammer have launched operations in the capital.
Everywhere you turn, the case for this being London's "moment" grows more compelling. Stanford and Berkeley Universities have long been hailed as one of the key ingredients in Silicon Valley's success, yet three of the world's top 10 universities – Oxford, Cambridge and Imperial College – are nearby, or in the capital itself, in addition to the London Business School, the LSE and Central St Martins. Southampton, a global leader in the semantic web and home to Prof Nigel Shadbolt and Sir Tim Berners Lee, founders of the Open Data Institute, is also little more than an hour away.
The UK now has one of the best environments globally for founders and angel investors. Thanks to a campaign by Seedcamp, Britain is the only G20 country with an Entrepreneur Visa, so that if you have £50,000 of accredited investment, you can come from abroad and start your business here. Similarly, the first £10m of an exit is taxed at just 10%, while the Seed Enterprise Investment Scheme (SEIS) allows backers to invest up to £100,000 in a single tax year, which can be spread over a number of UK companies, offering tax relief of 50%.
And perhaps most important of all: London plays host to at least 20-plus category breakout companies - including King.com, Just Eat Mind Candy, Mimecast and Wonga. These are all big businesses, still private and growing fast. Their rise is eye-watering; five years ago there were only four or five companies of that size in London (Asos, Lovefilm, Playfish, Skype). If present trends persist, in five years time there'll be 50. In a decade, perhaps, 100 – or more. If some of the current wave can go public, either here or even on the NASDAQ (and at least two of them are currently preparing for IPOs), then we will start to see companies on the scale of Facebook and Google headquartered in London, which would create tens of thousands of jobs.
This surge in growth is only possible because London is now not only the most international city on earth, but the peerless centre for European early stage capital. If a founder, with a promising business, took a 10-minute stroll around Mayfair, they'd have access to €5bn of early stage capital – and that's not just from Index: but from Accel, Balderton and Wellington. Indeed, tech investment is flourishing at every layer: from seed and Micro VC, thanks to Seedcamp and new micro VCs such as Hoxton Ventures, as well as London's traditional strengths in private equity, hedge funds and capital markets. So the cash is here, as are, crucially, people looking for investment opportunities.
And that certainly wasn't always the case. When I first returned to London in 2002 – after a decade in the US – I wanted to start an internet business. But Silicon Valley-style investors were thin on the ground back then. The turn-of-the-century internet crash had fostered a sense that the web was a fad and businesses built on it were no longer investable. The prevailing attitude, I recall, from the media, corporates and investors was: 'Thank God this internet thing is over. Now things can return to the way they were before.'
But they didn't, of course, and I can pinpoint the precise moment I felt a seismic shift. I had launched the DVD rental company Video Island (which would later become Lovefilm), when I was introduced to a group of Nordic founders, who were thinking of moving their HQ to London. My partner at Index Ventures Danny Rimer urged me to download their product, and aside from the day I first downloaded the Netscape browser 15 years earlier, I'd never seen anything as exciting. Skype's arrival was a genuine game-changer. Outside of the Valley and Seattle, this was the very first time I'd seen something that had the potential to be a global internet brand – and the fact that this was happening in London was truly amazing to me.
The years since, and the last five in particular, have seen the total transformation of the capital's technology landscape. Yet for London to retain its position as a world-beater, there's one statistic we should all be repeating, mantra-like, until it seeps into the national consciousness: the internet economy is worth more than 8% of UK GDP. With that in mind, investors of whatever shape or size should look at every company, not just in the FTSE100, but the EU500 too, and ask their CEOs: 'Do you do more or less than 8% of your business over the internet? If you don't, then I'll be shorting your stock. If you do, maybe I should be buying more of it.' Of governments, from the EU to regional administrations and local councils, we should be demanding that at least 8% of services are delivered online. If not, then they are failing tax-payers.
8% is what success looks like in the internet age. Anyone who is doing more than that, is growing faster than GDP. It really is that simple. The UK is in the vanguard of a worldwide technological revolution. We have a once-in-a-lifetime chance to cement London as one of the top five hub cities of the internet century. This is our moment on the global stage. Now all we have to do is perform.
Boot up: RIM's handset spotted

Sydney Harbour. Or is it? Photograph: Paul A. Souders/Corbis
BlackBerry 10 'L-Series' device fully exposed in new hi-res images, video >> CIO Blogs
The general appearance of Research In Motion's (RIM) first BlackBerry 10 smartphone, the all-touch "L-Series," is no secret; images and video of the upcoming handset have been slowly leaking for the past couple of months. But today, a Vietnamese tech site posted the first set of high-resolution photos of the BlackBerry 10 L-Series handset, along with a five-minute video that gives an in-depth look at the phone and compares it to RIM's Dev Alpha BlackBerry 10 developer smartphone and Apple's popular iPhone 5.
Fortune Exclusive: Larry Page on Google >> Fortune Tech
There's loads to ponder in this interview, but probably the most interesting is this:Q: So is there one thing that keeps you more occupied right now than any other thing?Read the whole thing, though.
The thing I'm most occupied with now actually is the overall structural questions. We want Google to be wildly successful. What does Google look like five years from now? What are we doing? Who's doing it? How are we organized? What people do we have? And I think we have some answers to those questions. But I think, like I said, what I'm trying to do is to get a technology company that continues to scale its impact and aspirations in its everyday. We're at a certain scale now, but I don't see any particular reason why we shouldn't be much bigger, more impactful than we are now.
Google chairman says Android winning mobile war with Apple >> Bloomberg
And Eric Schmidt also comments on this:The company avoided about $2 billion in worldwide income taxes in 2011 by shifting $9.8bn in revenue into a Bermuda shell company, almost double the total from three years before, filings show.
Governments in France, the UK, Italy and Australia are probing Google's tax avoidance as they seek to boost revenue. Schmidt said the company's efforts around taxes are legal.
"We pay lots of taxes; we pay them in the legally prescribed ways," he said. "I am very proud of the structure that we set up. We did it based on the incentives that the governments offered us to operate."
The company isn't about to turn down big savings in taxes, he said.
"It's called capitalism," he said. "We are proudly capitalistic. I'm not confused about this."
Android appears to infringe Nokia patent relating to multifunctional phone-computer USB connections >> FOSSPatents
Unless this patent is invalidated, which won't happen to the German part of this patent before 2014 at the earliest, it's hard to see how any Android device maker would not want to license it. Workarounds are possible but would come with reductions in functionality and/or easy of use for USB connections of smartphones and tablet computers to desktop computers.Which would logically add to the drag on profits for Android handset makers. It's starting to add up. This case is only against HTC but would easily extend to others.
Samsung knocks Apple Maps in Sydney marketing stunt >> CNET News
CNET Australia has snapped pics of a little guerrilla marketing by Samsung featuring a muddied-up vehicle with a tent and other camping supplies. Next to it is a sign that says, "Oops, should have gotten a Samsung Galaxy S III. Get navigation you can trust."That would be Google's maps. Read on... (Thanks @mopoke on Twitter for the link.)
Police warn of safety concerns from Google Maps >> ABC News
Now police in Colac, west of Melbourne, say faults with Google maps are putting people's lives at risk along the Great Ocean Road and in the southern Otways. Sergeant Nick Buenen says trucks, buses and tourists are being directed down Wild Dog Road, which is a one-way track, not built for heavy traffic.Google Maps in GPS? Anyhow, clock started. Australia seems to be the hardest place to map - keep reading...
He says VicRoads has denied responsibility and Google Maps has not responded.
"My issue is it's a significant safety issue for tourists [and] locals, who are getting the wrong information from their GPSs," he said.
"My concern is that one day we're going to be at the coroners court [being asked] well what did you do about it. We're trying to do something about it, but if a 22-seater bus rolls off Wild Dog Road today, [there wouldn't be] the multi-agency response to this issue that I would like."
Another Apple maps desert death trap down under >> The Register
Just when Apple thought it couldn't get any worse for its beleaguered Maps app, which has been leading motorists deep into the desert when they try to find the town of Mildura, The Register can reveal another SNAFU that could send travellers to an even less hospitable destination.Another case where you need human intelligence applied to the official gazetteer of Australian locations - which shows multiple entries for "Mount Isa"; some are population centres, some aren't. Google gets it right because it assumes that humans will be looking for other humans - that is, centres of population - and puts that top of the search results. Apple's offering has the populated location as its second result.
The site in question is Mount Isa, a town in the interior of Queensland. Famed for its colossal mines and attendant facilities, the town is home to around 23,500 souls.
Google sells Motorola's factories in China and Brazil to Flextronics >> Android Authority
Google, which officially acquired Motorola Mobility in May of this year, has just announced that Flextronics will acquire Motorola's factory Tianjin, China. Flextronics will also "assume the management and operation" of Motorola's factory in Jaguariuna, Brazil. Who exactly is Flextronics? You know how Foxconn is the largest company that spits out consumer electronics? Flextronics is the second largest. Assuming both companies get all the required approvals, this deal will close during the first half of 2013. Financial terms were not disclosed, though we expect them to be leaked rather quickly.And also Motorola's factory in Chennai, India, is being closed - taking out 76 jobs. The picture that emerges is of a company retreating extremely quickly from having its own manufacturing operations in favour of contract manufacturing.
The Dumbest Apple Rumor of the Year >> Gizmodo
Because this morning, the two worst rumor sources in tech found each other. Analysts met patents, and created a perfect storm of bullshit...Great use of the <blink> markup, which hadn't previously been seen in the wild since 1995.
The problem with taking patents at face value is that patents aren't products and, more importantly, are often never even intended to be. Companies file patents defensively, stockpiling them like warheads for the never-ending infringement wars. They are, in their own way, every bit as Not Even a Thing as iTV itself. That's what every single one of these "features" is based on.
How can I protect my privacy online?

DuckDuckGo is good way to protect your privacy
During the summer, after booking a hotel room, I quickly received two or three emails with the subject "Booking confirmation". They were obvious spams from the poor quality of the content.
I am used to spam, and know how to deal with it. What concerns me is the apparent link between my activities and the content of the spams. It makes me feel as if there is an automated "watcher" waiting to see if I use certain sites then sending relevant spam.
I am running Windows Vista Business SP2 with Windows Defender, and for extra security, I manually scan with Malwarebytes Antimalware about once per week. Everything is up-to-date. Rob Cameron
I suspect these are coincidences. Billions of spam emails are sent every week, and you may well receive hundreds of legitimate emails each week. They almost never coincide, but we are pretty good at spotting when they do.
In this case, all the emails were spam, and the first one was part of a virus attack. A quick search on the attachment's filename finds Graham Cluley, our old friend from Sophos, identifying the malware as a Trojan (Troj/BredoZp-S) and warning against it.
But I would not have been surprised if the various emails had turned out to be genuine. Data tracking has been getting more and more sophisticated over the past few years, while users have been getting more predictable, thanks partly to broadband internet connections that keep you on the same IP address for months or even years.
Some websites now use software that can identify visitors by name, using tracking cookies (small text files websites store on your hard drive), internet addresses, and forms filled in at other sites. (See, for example, You're not anonymous. I know your name, email, and company, and Nowhere to hide: Advertisers can now stalk you across multiple devices.)
Google is the web's biggest advertising company and one of the most obvious trackers. It uses a huge network of ads that are shown across millions of websites, DoubleClick ad-tracking, the Play marketplace on Android phones and Google Search on Apple iOS devices – unless you opt out. It also looks as though the main purpose of its Google Plus website is to get users' real names and other accurate data, which Facebook has but won't provide to Google.
Facebook has also extended itself across much of the web using Facebook Connect and Like buttons. Users can log on to participating sites using their Facebook identity, and this gives these sites access to some information from their Facebook profiles. This is handy but less private than using different IDs for different sites, or using throwaway IDs and passwords from Bug Me Not.
The latest Web Privacy Census by the UC Berkeley Center for Law and Technology found the most popular 100 websites dropped thousands of cookies (6,485 on 24 October), and that 84.7% of them were third-party cookies. In other words, most cookies were not used by the site you visited (Amazon, Twitter etc) but by advertising and tracking companies such as Google's doubleclick.net (the biggest, dropping 69 cookies), scorecardresearch.com (54), and bluekai.com (41).
So yes, there's a whole host of "automated watchers" waiting to see if you use Amazon/your bank/hotel booking sites etc, and they may "spam" you with targeted advertising or perhaps legitimate email offers. (The companies argue that it is better to show you ads about things you are interested in, and they have a point.) Given that there are several hundred tracking companies, it would be surprising if there wasn't some "leakage" into less legitimate approaches, though I've not seen any evidence of this happening. However, hacking is always a possibility.
Several companies offer software to control or block cookies, and most web browsers let you block third-party cookies selectively. This means you can keep the website's cookies that, for example, remember which pages you have viewed while blocking the trackers. Two free ones I use are Abine's DoNotTrackMe and Evidon's Ghostery. The Electronic Frontier Foundation (EFF) also has an interesting project called HTTPS Everywhere, which uses a Chrome or Firefox extension to redirect some popular websites (Google Search, Wikipedia) over secure connections without breaking anything.
You can also load sites such as Gmail, Google Plus and Facebook using each browser's "private browsing" feature. This is called InPrivate Browsing in Microsoft's Internet Explorer, Incognito in Google Chrome, and Start Private Browsing in Firefox. While it's not practical to block all cookies, you can set each browser to delete cookies when you close it, which you should then do every couple of days. This will make the web less convenient, and you will have to enter passwords more often, but it will help increase your privacy.
Further, avoid using search engines like Google, which save your searches and send data to websites. Some alternatives are designed to protect your privacy, such as DuckDuckGo. This has an easy-to-read explanation at donttrack.us. If you absolutely must have Google search, access it via Ixquick's Startpage. This is a secure (HTTPS) page that sends your search to Google but throws away your search data and all the tracking information. (It also has a "family filter" which makes it a good search engine for kids.)
Another way to protect your privacy is to use an anonymous browsing service, though the free ones greatly limit what you can do online. I often use AnonyMouse and Hide My Ass!, which set up an encrypted "virtual private network" (VPN) between your PC and their servers. Websites get loads of hits from these anonymous servers, but can't identify you from thousands of other users.
VPNs are a particularly good idea when using public networks such as Wi-Fi hotspots. See my earlier answer, Using a VPN to protect your web use, for more details.
Finally, although you say "everything is up-to-date", I'll bet it's not. If you run Secunia's Personal Software Inspector (PSI), it will probably find half a dozen programs that need updating.
This may well include Google Chrome and various Adobe programs, Apple's QuickTime and Oracle's Java. PSI finds the non-Microsoft programs that are not up-to-date, provides links that you can click to update them, and charts your progress week by week
Inscription à :
Articles (Atom)